Cybersecurity Analyst Job Description & Role Breakdown

We all know the broad strokes of what cybersecurity professionals do in their day-to-day — they fight cybercrime, patch vulnerabilities, and protect our data. But ask the average layperson to get into the nitty-gritty details of a cybersecurity analyst job description, and they’ll probably draw a blank.
While most know that cybersecurity analysts strive to keep people safe online from hackers and scammers, most don’t have a clear idea of what goes into that protection, or of the wide variety of security tasks that cybersecurity professionals execute daily.
Unsurprisingly, there’s a lot more to a professional security analyst’s daily task list than the industry’s logline implies. If you’re interested in making a name for yourself in cybersecurity, read on! We’ll explain what you can expect from an entry-level cybersecurity job description, review the qualifications you’ll need to have as a candidate, and address the responsibilities you’ll face when you land your first role.
Let’s get started!
Cybersecurity Analyst Job Description
So, what does a cybersecurity analyst do? A cybersecurity analyst typically works within an organization such as a corporation, a government agency, or a non-profit, and strives to keep their employer’s sensitive, proprietary, and personal information safe from threats.
In this job, a security analyst works within a team to identify flaws in their employer’s security systems and proactively develop solutions. Their investigations aren’t solely concerned with preventing exterior threats; often, an analyst will also assess risks to the company’s internal network and physical offices.
The cybersecurity analyst job description also includes examining reports, data, and analytics to identify suspicious activity and threats. Analysts then use that collected information to develop protections and inform their company’s choice of security software.
They may also provide advice to company leadership on what they can do to improve their security and organize training programs to help non-technical employees better understand and adhere to the organization’s security policies.
A cybersecurity job description falls within the IT sector’s jurisdiction. This job is well-suited to tech-savvy professionals who enjoy creatively thinking about new solutions, coding, and exploring new tech. A solid understanding of how systems and networks operate can be critical to success in the field. As part of your job, you might be expected to do the following:
- Monitor computer networks and systems for threats and security breaches
- Install, alter, and update security software and firewalls
- Test systems for potential vulnerabilities
- Develop systems and processes for security best practices throughout the company
- Prepare reports on security incidents and changing responses
Even entry-level cybersecurity analysts are expected to do and know a lot. So, how can you prepare for the role, and what training do you need to thrive? Let’s discuss the most important qualifications you need before you start applying.
Qualifications
Entry-level role or not, a cybersecurity analyst position requires qualified candidates with the right mindset and a significant amount of technical knowledge. In the cybersecurity field, you maintain at least some responsibility for protecting systems even in an entry-level position, so having a firm foundation of skills is essential.
Those who take on a cybersecurity analyst’s role don’t just need technical skills; they also require “soft” skills such as analytical thinking, problem-solving, attention to detail, and critical thinking.
Some of the qualifications that may turn up on a cybersecurity analyst job description include:
- A bachelor’s degree in computer science or an educational equivalent
- Experience in working with information security or other relevant work experience
- Knowledge of penetration testing, network security, and the techniques used to expose and correct security flaws
- A broad understanding of security technologies including firewalls, proxies, SIEM, antivirus software, and IDPs
- The ability to identify and spotlight vulnerabilities on on-premises and remote networks, correct problems, and prevent security breaches
- Responsibility and conscientiousness, including proper management of patches to defray business impact while keeping security protocols up-to-date
- The ability to think critically and innovatively about the security solutions that can keep data safe while still allowing a business to flourish
While having a college degree is useful, it is not always necessary for success, especially if you have significant experience, a degree in an unrelated field, or additional specialized training. According to a 2018 ISC(2) Cybersecurity Workforce Study, only one-fifth of employers viewed a “cybersecurity or related undergraduate degree” as one of the most essential qualifications for employment.
The same researchers further note that employers view several qualifications as more important than a specialized college degree: 47 percent of those surveyed identified knowledge of advanced cybersecurity concepts as the most crucial qualification a candidate can have, while 43 percent indicated cybersecurity certifications and 39 percent named strong non-technical and thinking skills.
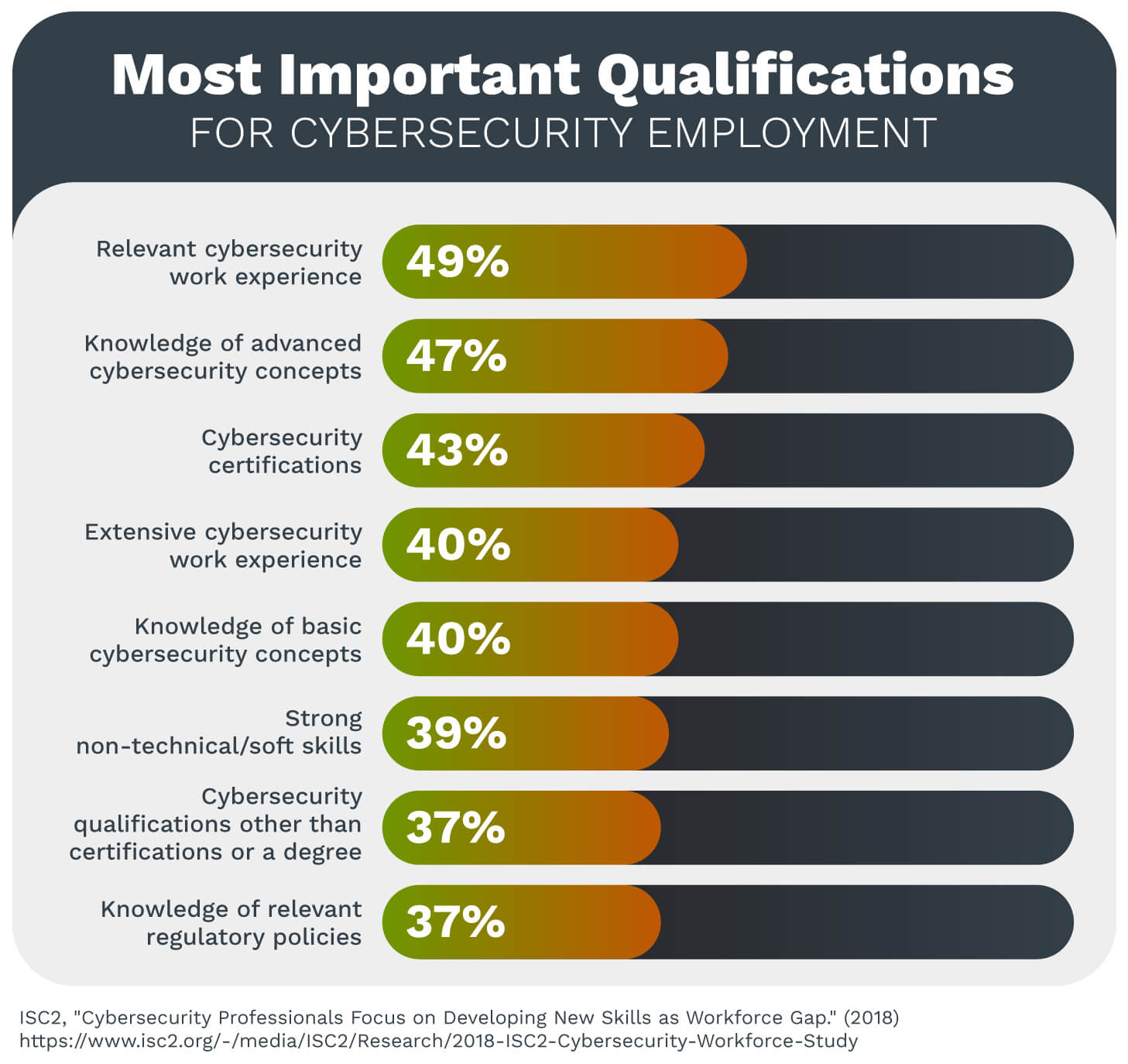
These statistics indicate that even if your undergraduate education was unrelated to cybersecurity, you can still develop the skills you need for cybersecurity success.
If you don’t have the time or money for a conventional four-year degree — or you already went to university and are looking for a career change — other academic routes can prepare you equally well for a career as a cybersecurity analyst.
One such choice is a cybersecurity boot camp program. Many boot camps can guide you through the training you need to secure valuable cybersecurity certifications, all in a matter of months, not years. A boot camp is a quick, skills-based program designed for learners who want to efficiently improve their practical knowledge and upskill for a new career.
Boot camp programs tend to be more flexible than four-year degrees, too, with part-time and virtual courses that can appeal to students who need to learn while maintaining a job or caring for children at home.
Need an example? Look no further than The Cybersecurity Boot Camp at UT Austin. This 24-week program includes security fundamentals, system administration, networking and network security, and defensive and offensive security. It offers final projects that students can use to build their portfolios while helping them prepare for crucial cybersecurity certification exams.
Responsibilities of the Role
Which responsibilities are absolutely central to any cybersecurity analyst job description? Not all cybersecurity analyst roles will be the same, but most entry-level professionals commonly take on the same core tasks.
1. Investigating Security Breaches
Data breaches can be devastating for a company. When these events occur, they can compromise public and consumer trust; in the worst cases, they can cost thousands or millions of dollars and lead to credit card fraud, identity theft, or other severe financial losses. As a cybersecurity analyst, it falls to you to investigate security breaches to identify malicious hackers and harden your organization’s security.
Cybersecurity analysts are responsible for conducting digital forensics at a digital crime scene. You’ll need to identify whether a real or attempted breach occurred, look for lingering security flaws or malware left behind, and try to recover data. If you have a talent for investigation, you may even wind up working for a firm that specializes in digital forensics.
2. Working With a Team to Locate Vulnerabilities
What does a cybersecurity analyst do? One of the most important aspects of the job is finding vulnerabilities so they can be corrected before a breach occurs. You may perform a vulnerability assessment to identify potential threats to organizational security. During this assessment, you’ll spotlight the data and assets at risk and list the possible reasons for a future breach.
Teamwork is essential here — not only with other members of the IT team but also with the other non-technical staff members whose jobs might be affected by a lapse in security. Cybersecurity analysts need to maintain open communication lines so that they can teach their non-cyber peers what they need to know about updated cybersecurity protocols and how to protect themselves from outside attacks.
3. Performing Ethical Hacking
Ethical hacking is another tool of the trade for security analysts. With this practice, cybersecurity professionals aren’t aiming to break security to steal data themselves; instead, they seek to identify security holes and correct them before they can be leveraged by bad actors. For people who love problem-solving and untangling challenging security issues, penetration testing can be one of the most exciting parts of the job. You might use software applications or your manual coding skills to, essentially, hack and exploit your own system to determine how to fix it.
You might use tools like Kali Linux and Metasploit for penetration testing, robust software programs that expose and probe vulnerabilities across operating systems. While security professionals designed Kali Linux, Metasploit is used by both cybercriminals and ethical hackers to identify the same weaknesses — with conflicting goals.
4. Installing and Operating Security Software
Managing, installing, and operating security software is a critical part of the cybersecurity analyst’s role.
As a cybersecurity analyst, you might install system-wide software for better email or login security, prevent malware from crossing into a network from an individual computer, enhance security for mobile devices, or strengthen your network’s shield against unwelcome intrusions. You may also use specialized software to improve your penetration testing, shield your company website, and guard network traffic.
A cybersecurity analyst also needs to ensure that only the people who should access sensitive data have access to those systems.
One of the most critical aspects of this task is identity and access management (IAM). When implementing IAM, analysts ensure that each user on the network is appropriately identifiable and that their network access levels are what they need to be while limiting the system’s exposure to security problems.
Some of the most severe ransomware incidents of recent years were caused when non-tech-savvy employees inadvertently downloaded malware. Proper identity and access management can — when well-implemented — mitigate this risk.
5. Developing and Implementing Organization-Wide Security Protocols
As a cybersecurity analyst, you will develop security protocols for an entire organization and its digital ecosystem. Today’s systems administration and networking jobs strongly prioritize cybersecurity and protection.
Because security applies to everyone, no matter now non-technical their jobs, security protocols must be understood and followed by every person in an organization. As a cybersecurity analyst, you’ll develop these protocols — all the while remembering that the network is only as strong as its weakest security links.
What Are My Prospects As a Cybersecurity Analyst?
Job prospects for cybersecurity professionals are fantastic across the board. According to the Bureau of Labor Statistics, jobs in this sector are expected to grow by 32 percent between 2018 and 2028. This rate is over six times the average for all other jobs, which currently sits at 5 percent.
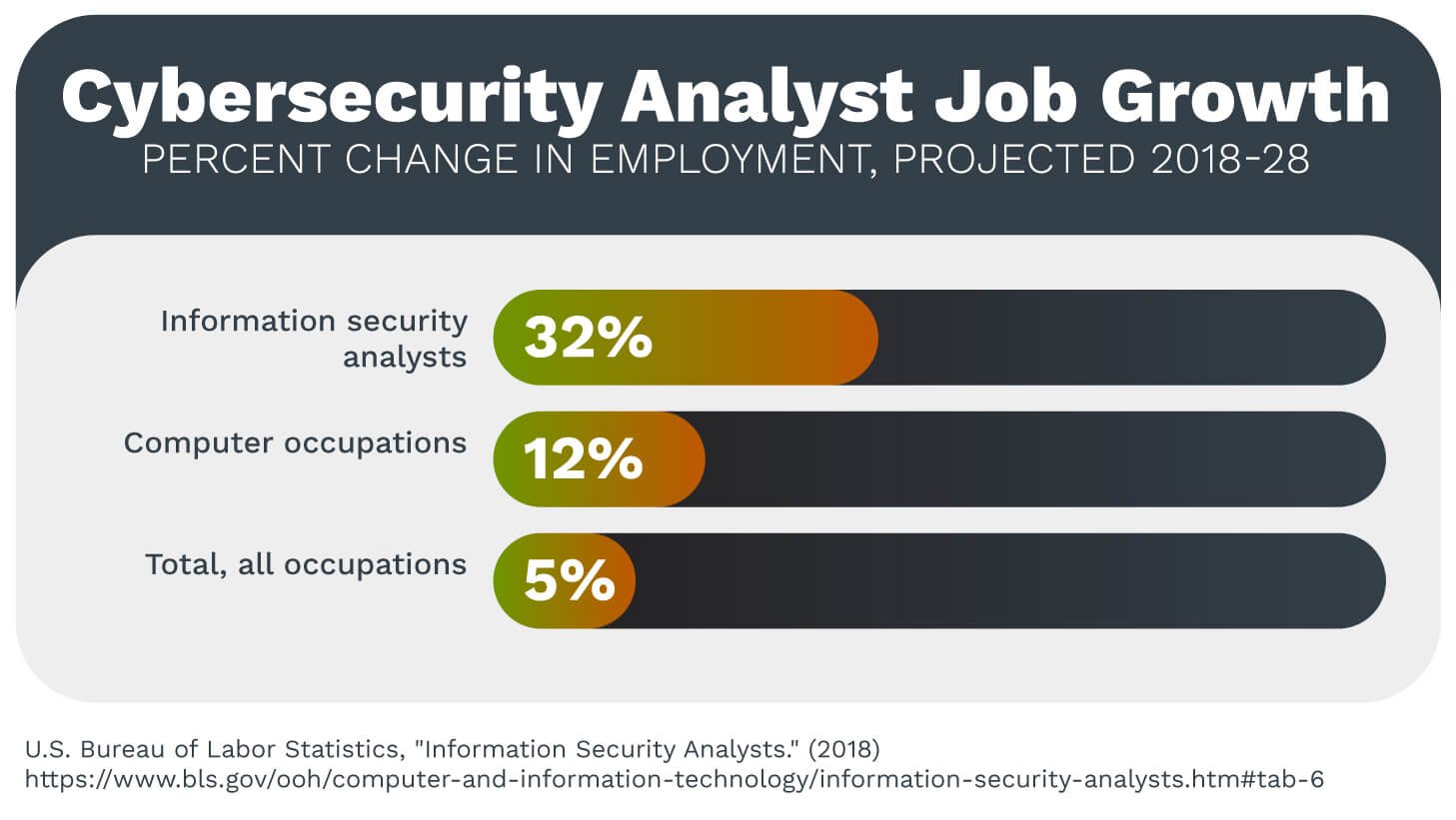
This job growth reflects a broader upward trend in the cybersecurity field as a whole. In 2019, a report published by (ISC)2 noted that the workforce gap for cybersecurity professionals is almost 500,000 in the U.S. alone. The American talent pool would need to grow by 62 percent just to meet the nation’s current need for cybersecurity talent.
With such an intense need for talent, aspiring cybersecurity professionals have terrific career opportunities. By upskilling and entering the job market now, you could have the chance to build a satisfying and rewarding career in a fast-expanding field. As a newly minted cybersecurity candidate, you’ll be joining an industry with exciting tasks — even in an entry-level position — and massive upside for potential future growth.
If this sounds like the right fit for you, start your journey into the cybersecurity field by looking into your educational options. It will be the first step toward building a stable, exciting, and satisfying career.

 Live Chat
Live Chat