Getting Into Cybersecurity With a Nontechnical Background

Want to know the best-kept secret in cyber? Well, here it is: You don’t need to be a tech wizard to thrive in information security.
Yes, yes, we know; even writing it feels a little slanderous. Nontechnical cybersecurity backgrounds? The phrase seems like a contradiction in itself.
Hollywood stereotypes suggest that cybersecurity pros spend their days in darkened computer labs, digging through endlessly scrolling pages of code in search of a rogue virus or black hat hacker’s malicious program. They speak in fluent technical jargon and usually prefer their code to any human company. Being tech-savvy isn’t just a prerequisite for the job; it’s a defining trait.
Or is it? As it turns out, having a technical background may be less important than you think.
Here’s why:
There are other ways to get your foot in the proverbial door. While the majority of cybersecurity professionals (77 percent) have a background in IT, many don’t. According to Enterprise Strategy Group’s report on The Life and Times of Cybersecurity Professionals (PDF, 1.2 MB), a full 23 percent of surveyed cybersecurity employees originally began their careers in a non-IT field.
It’s worth noting, too, that the number of non-IT cybersecurity professionals is poised to grow. There is currently a worldwide shortage of cybersecurity employees. The market analytics firm Burning Glass reports that the number of cybersecurity job postings has grown a whopping 94 percent since 2013 (PDF, 3.5 MB) — a stark increase over the 30 percent growth reported for IT positions in general.
But this fast-paced expansion hasn’t come without its fair share of growing pains. The increasing demand for cybersecurity services has far outstripped the available talent pool. According to (ISC)2 research (PDF, 1 MB), the shortage of cybersecurity professionals is nearly three million globally. In North America alone, that shortfall encompasses around 498,000 unfilled positions.
The researchers further note that the talent shortage has already had a real negative impact on businesses. A full 63 percent of surveyed respondents say that their organizations need cybersecurity-dedicated IT staff. Nearly 60 percent claim that their companies are at moderate or extreme risk of cyberattacks due to the lack of available talent.

This lack makes it necessary for companies to hire talented staff when they can, even if candidates’ educational backgrounds are a little unconventional.
As Vyas Sekar, an associate professor of electrical and computer engineering at Carnegie Mellon’s Cylab, once commented for CNBC: “I think we have perpetuated this myth that cybersecurity is based on this hacker stuff, sitting in a basement and only working on technical things. In fact, it’s those with an analytical mindset that can do very well in the cybersecurity field. The sort of basic computer science that is necessary can be taught later.”
The truth is, getting into cybersecurity with a nontechnical background isn’t just possible — it’s encouraged. Nobody explains this point better than Deborah Hurley, a cybersecurity professor at Brown, who commented for TechRepublic: “Sometimes, it’s perceived that the only way of entering cybersecurity is through the technical door, but that’s not the case. Whatever a person’s talent, with people, administration, management, education, or technology, there is almost certainly an aspect of cybersecurity for which their skills and experience are needed.”
Below, we explore a few nontechnical cybersecurity backgrounds and explain how you can build a thriving career in the industry.
Common Nontechnical Backgrounds
Technical Writing
Many professionals with nontechnical cybersecurity backgrounds find entry into the field relatively easy because many of the core skills for cyber writing are identical to those in other technical fields. Technical writing refers to the practice of detailing and documenting complex software systems. In cybersecurity, technical writing — the ability to communicate and clarify processes — is a vital skill.
In a writing role, the cybersecurity technical writer will be responsible for helping their organization better understand cyber-bound threats and security objectives. Typically, technical writers who specialize in cybersecurity are tasked with creating technical manuals, synthesizing data, and converting security strategies into clear, well-defined policies.
However, these professionals are not limited to writing roles; those with technical writing experience can apply their trained talent for decoding complex concepts to help them quickly grasp new cyber concepts during training, as well as communicate with non-cyber professionals.
Additional Resources:
- Hack the Reader: A Cybersecurity Writing Course — SANS
- From Studio Arts Major to Technical Writer: My Unlikely Journey — CMD Security
- Technical Writing For Dummies — Sheryl Lindsell-Roberts
Project Management
Contrary to popular thought, a big company’s cybersecurity department doesn’t consist of a sole computer whiz thwarting hackers’ attempts.
A professional with project management experience can coordinate disparate efforts between IT professionals, security staff, product developers, and extra-departmental business entities. Project managers are big-picture thinkers; their role is to use the resources, talent, and company initiatives at hand to get an organization’s security framework up to par.
A cybersecurity department usually encompasses a team of specialized professionals, all of whom work on different technical security aspects. But like any well-constructed team, cyber departments need a talented project manager to assign deliverables, deploy talent, and ensure that employees are being used to their maximum potential. Cybersecurity pros with project management experience can leverage their prior experience to fast-track their promotion potential and excel in security management roles.
Additional Resources:
- What is Project Management? — Project Management Institute
- Why Project Management Is Crucial to Cybersecurity — CompTIA
- 8 Cybersecurity Jobs That Require Project Management Skills — CompTIA
Law
If and when customer data leaks, it falls to law professionals to serve as intermediaries between a corporate employer and governmental officials.
All businesses need to adhere closely to compliance law. Because of this, larger operations will often onboard cybersecurity law professionals to mitigate risk and keep operations compliant with evolving security laws. In their day-to-day work, these legally minded cybersecurity employees will analyze current cyber laws and create common-sense policies that comply with federal and state laws.
Are you interested in making cyber law your focus? Lawyers can get certified by taking courses about compliance and cyber law. If you have a legal background and are interested in making cyber law your focus, consider taking courses about cybersecurity compliance, as well as international and domestic security law.
Additional Resources:
- Cybersecurity Lawyers Are in High Demand With Little Competition — Law.com
- Have a J.D. but Don’t Want to Work in Law? Consider Cybersecurity — FindLaw
- Cybersecurity Education for Lawyers — Law.com
Finance
Do you already have an educational or career-based background in finance? Your nontechnical cybersecurity background may make you ideally suited for working in cybersecurity.
Banks and other institutions that store customers’ payment information need cybersecurity employees who understand the ins and outs of financial analysis. Thus, it might be easier than you think to transition to the technical field if you’re already familiar with financial risk analysis.
Many financial experts transition into cybersecurity gradually; according to CyberSeek, it is common for those with finance backgrounds to first become IT auditors before progressing through cybersecurity consultant roles and system architects positions.
Additional Resources:
- From Financial and Risk Analysis to Cybersecurity: Choose Your Own Adventure — CompTIA
- Cybersecurity Career Pathway — CyberSeek
- Accountants Are Moving Into Cybersecurity — Careers in Cyber
Security and Law Enforcement
Military veterans or those who hail from law enforcement are well-positioned to break into the cybersecurity sector.
Careers in law enforcement develop skills like situational awareness, intelligence gathering, and adhering to security protocols. These skills are valuable in private-sector cybersecurity professions because cybersecurity requires constant threat analysis and the application of problem-solving skills to address evolving security situations.
In fact, if you have hands-on experience in roles that require sophisticated tech or governmental clearance, you may even have a leg up over your competition! While availability varies by military branch and program, some veterans’ programs offer transitional support services for ex-servicemembers to move into a cyber career. Similar upskilling opportunities may be available for those working in police precincts or federal enforcement agencies.
If you have military or law enforcement experience and want to move into cybersecurity, check in with your local organizers to see if you’re eligible for some educational assistance!
Additional Resources:
- The Emerging Cyberthreat: Cybersecurity for Law Enforcement — Police Chief Magazine
- Why Police Need the Skills to Counter Cybercrime — Raconteur
- Skill Sets for Transitioning into a Cybersecurity Career — Security Boulevard
You Don’t Need a Degree to Get Started
Most assume that they’ll need, at the very least, a four-year degree in IT or cybersecurity to start building their career. College degrees can undoubtedly be helpful; however, a formal undergraduate program isn’t the only educational route at your disposal.
Recent research indicates that skills and certifications may be more important to employers than a formal degree. According to a 2018 report from (ISC)2 (PDF, 1 MB), only 20 percent of hiring managers view a cybersecurity or related undergraduate degree as “one of the most important employment qualifications” for employment.
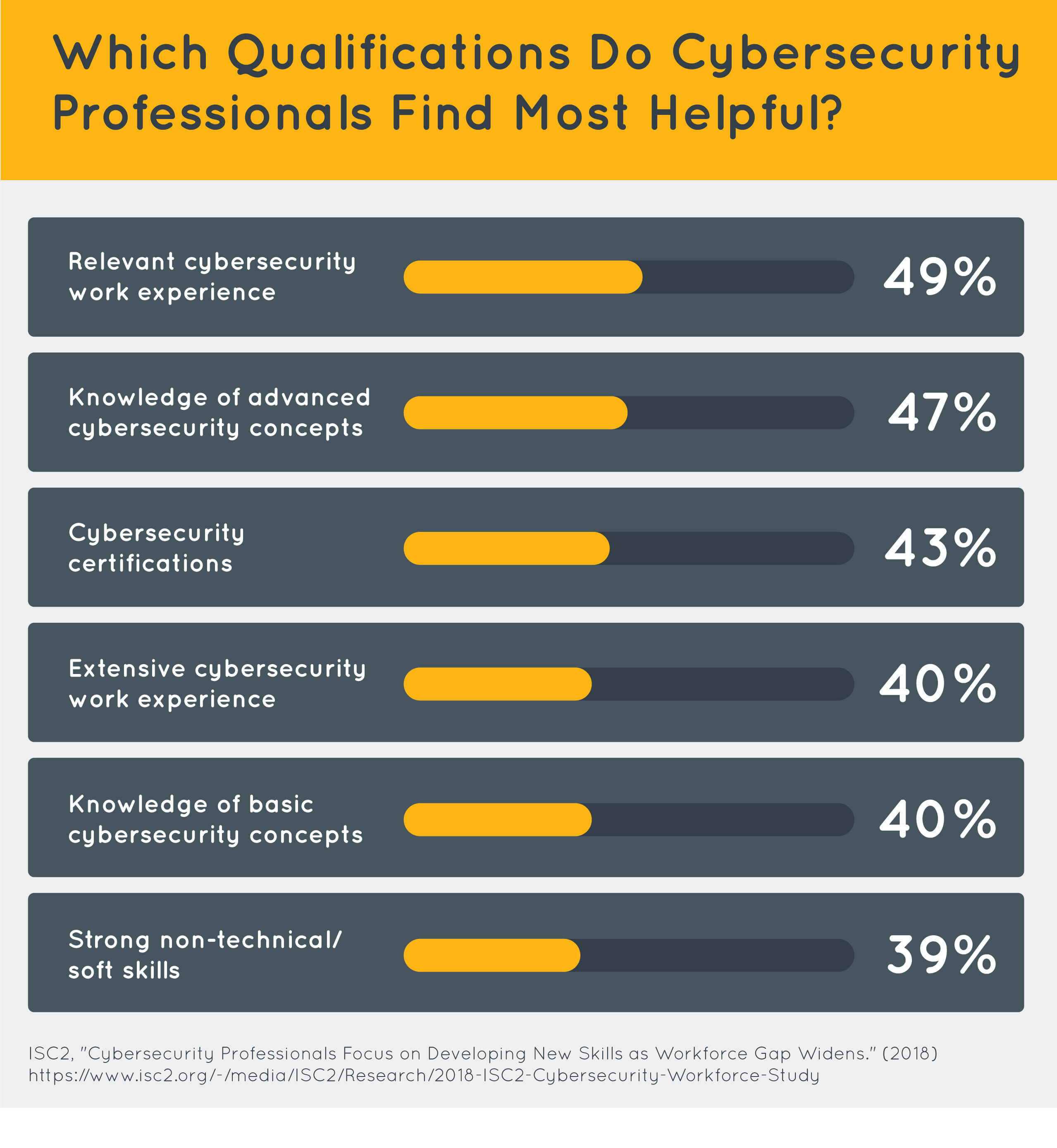 Employers want to know that their employees have cybersecurity knowledge — how they acquired that experience is a less-pressing concern. You don’t need to earn a four-year degree or go through a master’s program to get your foot in the door; once you have the requisite technical skills and experience, you can thrive in the industry.
Employers want to know that their employees have cybersecurity knowledge — how they acquired that experience is a less-pressing concern. You don’t need to earn a four-year degree or go through a master’s program to get your foot in the door; once you have the requisite technical skills and experience, you can thrive in the industry.
Technical Certifications and Skills to Pick Up
Certifications offer one of the most straightforward ways for job candidates from nontechnical cybersecurity backgrounds to prove their skills. While it’s unnecessary to collect every certification out there, picking up a few of the most popular and position-relevant ones could significantly boost your job prospects.
According to statistics provided by the 2020 Global IT Skills and Salary Report, a full 96 percent of IT leaders believe team members with cybersecurity certifications add value to their organizations.
Keep in mind that the certifications you decide to pick up will vary based on your role and aspirations. As Leo Pate, an application security consultant, recently commented for DICE Insights: “[Choosing a certification] depends on what you’re trying to learn and where you are going to work. Not all certifications are created equal, so make sure the one you are spending time, money, and energy into obtaining is ‘worth’ it.”
Here are a few popular certifications to consider in your research:
- Certified Information Systems Security Professional (CISSP)
- Certified Information Systems Auditor (CISA)
- Certified Information Security Manager (CISM)
- CompTIA Security+
In addition to the above, you’ll need to pick up at least a few of the following technical skills:
- Networking
- Systems Administration
- Risk Management
- Cloud Security
- Identity and Access Management
- Ethical Hacking
- Digital Forensics
- Vulnerability Assessment
That said, hard skills and certifications alone won’t guarantee your employment. To boost your chances of landing a job, you should also focus on improving your soft skills.
Soft Skills You May Need
When you’re in the throes of applying for technical work, it’s easy to overlook some of your best assets: how you approach your work, interact with colleagues, and deal with day-to-day stresses on the job.
Hiring managers want to work with job candidates that can handle problems with grace and mesh well with their office culture. According to (ISC)2 research (PDF, 1 MB), over a third (39 percent) of hiring managers felt that a person’s soft (or nontechnical) skills were among the most important qualifications to consider when making a hiring decision.
Below, we’ll outline the most relevant nontechnical skills to cybersecurity. If you come from a nontechnical cybersecurity background, the good news is you likely have a good grasp on some of these already!
Research and Writing
Cybersecurity professionals need to be able to document and incorporate current security practices and research into industry standards. Because threats continually change, cyber pros fight in a technological arms race to keep malicious actors from breaching private corporate data.
Cybersecurity professionals should be able to clearly express ideas through the written word. Technical writers are especially well-aligned with the skill set, owing to their background in processing scientific reports and documenting processes.
Additional Resources:
- How to Write Clearly About Complex Topics — Forbes
- So, You Want to Be a Security Researcher? — Dark Reading
- Technical Writing Courses — Google Developers
Collaboration
Cybersecurity is a broad practice that requires professionals to protect a range of networks, devices, device drivers, and databases from unauthorized criminal access. Besides collaborating interdepartmentally, cybersecurity employees will need to communicate consistently to the developers that handle database information and business logic.
Emerging threats will require the full attention of the entire business. At the end of the day, it only takes one employee clicking on a phishing link in their email to make a business vulnerable to threats. Cybersecurity professionals need to drum up support and communicate clearly between themselves, with company stakeholders, and with employees that don’t have technical knowledge.
Additional Resources:
- Three Ways to Collaborate to Improve Cybersecurity — IBM
- 5 Ways to Develop Your Workplace Collaboration Skills — Robert Half
- Cybersecurity is About Teamwork, Not Individuals — Security Boulevard
Interpersonal Networking
Cybersecurity isn’t just about computer networking; it’s also about networking with people. No matter the career field, all professionals need to develop sturdy connections to those around them. Company officials and employees are much more likely to adhere to new security guidelines if a relationship of trust exists between them and the cybersecurity professional.
Moreover, it’s much easier to break into cybersecurity if you have a connection who already works in the field. Then, rather than blindly filing dozens of online job applications and hoping for the best, you can ask real employees for company insights and advice before you apply.
Those coming from legal compliance or law enforcement may be better positioned to make these connections, as they have already developed their interpersonal networking skills in the legal field. After all, lawyers need to create links to individuals from many walks of life to understand their clients and build a convincing case. These polished skills make former lawyers and legal professionals well-suited to building bonds in cybersecurity.
Additional Resources:
- Top 50 InfoSec Networking Groups to Join — Data Insider
- 10 Reasons Why Networking Is Essential For Your Career — Forbes
- 18 Easy Networking Tips You Can Use Today — Science of People
Problem-Solving and Analytical Thinking
In recent years, issues like Cloud vulnerability and AI-enhanced cyber threats have risen to prominence. As more sensitive data is stored on third-party servers and malicious hackers are better able to form adaptive software, it falls to cybersecurity professionals to think through and solve these challenges. In this context, problem-solving and analytical thinking refers to the discipline of breaking up complex problems into their smaller components and solving them.
While many backgrounds provide experience in identifying problems under pressure, some (law enforcement, for example) are particularly suited to teaching professionals how to address criminal behavior and problem-solve tricky hacking attempts. That said, you can develop your problem-solving abilities in every industry — so don’t forgo the opportunity to do so!
Additional Resources:
- Cybersecurity Requires ‘Insatiable’ Problem-Solving Skills — Wall Street Journal
- 10 Ways to Improve Your Problem-Solving Skills — CMOE
- 6 Techniques to Better Your Problem-Solving Processes — Inc.
Empathy
Empathy is one of the most-needed (and rarest) skills found in cybersecurity.
In cyber, one of the biggest threats is not hackers coming from outside the organization — it’s those from inside who ignore security protocols. Let’s face it; we all know someone who uses a password like “123456” and “qwerty” despite the well-established risks of using such a common code.
As a cybersecurity professional, you’ll need to understand why people make the decisions that they do. You’ll need to understand the context for their choices and develop human-centric security policies that take your understanding of human decision-making into account.
Additional Resources:
- Empathy is a Cybersecurity Necessity — Intuition
- Empathy Matters: Leadership in Cyber — Just Security
- 16 Ways To Train & Increase Your Empathy — Cognition Today
Where to Learn Technical Skills
Take a few moments today to sit down and assess the technical and soft skills your previous positions have imparted. What skills do you have that could bolster your career in cybersecurity? What skills have you yet to hone?
Once you have a list of the soft and hard skills you already have, you can start figuring out how you want to obtain the rest of the practical knowledge that you need to succeed in a cyber role.
Which educational path should you walk on your way to become a cybersecurity pro? We’ve included a few options below, but the choice is ultimately up to you. That said, you should always remain confident that getting into cybersecurity with a nontechnical background is both possible and encouraged.
Self-Directed Learning
In the Information Era, it’s possible to learn everything under the sun online. A wealth of free or inexpensive e-books, articles, Youtube tutorials, and self-guided online courses make it easy to pick up critical cybersecurity skill sets.
Keep in mind that it requires no shortage of discipline and perseverance to embark on this educational route. Without any formal structure or guidance, it’s easy to end up spending too much time on low-quality materials (or on not learning at all).
To avoid this motivational hurdle, we suggest joining online communities or picking up a cybersecurity hobby with a friend. It’s easier to stay inspired if you have support from a social network.
Boot Camps
Boot camps are intensive, short-term learning programs that equip students with the industry-ready skills they need in as little as three to six months. Unlike self-directed study, students in these programs have access to peers and mentors who can provide feedback and offer structured coursework.
Boot camps also typically require less time and tuition than a conventional four-year degree. That said, boot camps don’t provide the same theoretical depth as a college education will.
If you want to make a career change as quickly as possible and prefer a structured environment, a cybersecurity boot camp may be the right choice for you.
Degree
Don’t have your degree yet? You might want to consider a degree in computer science, IT, cybersecurity, or a related discipline. During college, you’ll have ample time to explore the field, develop long-lasting connections in the industry, and establish a fantastic portfolio for future employers.
All that said, college tends to be more cost-intensive than the other learning routes mentioned here. If you have preexisting professional or personal obligations that make a four-year, full-time commitment difficult, consider enrolling in a boot camp or taking a more self-directed educational route.
How to Find a Job Once You’re Ready
Once you finish your chosen educational program, you face a new hurdle: finding a job.
It doesn’t matter if you’re an industry veteran or a relative newbie — job hunting is intimidating. Luckily, the search is skewed in your favor; as we mentioned at the start of this article, the shortage of cybersecurity professionals stands at nearly three million globally (PDF, 1 MB) and seems likely to grow in severity over the next several years.
Employers need your talent. The trick is proving that you have it to begin with.
Network, Network, Network
Your first step should be to build a robust professional network. According to statistics provided by CNBC, up to 80 percent of job openings are filled via personal or professional connections. Like most of us, employers tend to gravitate toward people they know, like, and trust.
If you want to get into that vaunted pool of probable hires, start forging connections! Build out your LinkedIn network; start attending networking events and conferences. The more you can establish a presence in cybersecurity circles, the more qualified you’ll appear to interviewers.
Apply Ambitiously
It’s well-established that imposter syndrome hits many of us hard during the job search process. Don’t let unwarranted anxieties keep you from selling yourself!
Apply to jobs you want even if you don’t tick every box in the description. Often, employers are looking for people who will be hardworking, learning-minded employees. Given the choice, they would probably choose a driven but less-experienced candidate over one who technically meets requirements but fails to go the extra mile at work.
You’ll never land your dream job if you don’t put yourself out there.
Tailor Your Application
Take some time to review your resume, craft a top-notch cover letter, and thoughtfully prepare for each interview. Ask yourself:
- What could I, specifically, bring to this role?
- Are there any concrete examples in my past jobs that I can point to during my interview?
- What makes me a fit for the company from a cultural perspective?
Whatever you do, don’t take a cookie-cutter approach in your applications — a hiring manager will see right through it!
Final Thoughts
Popular misconceptions hold that getting into cybersecurity with a nontechnical background is impossible.
That simply isn’t true; if you have an interest in protecting companies and consumers from cybercrime and are willing to spend some time upskilling, you can absolutely break into the field.
The cyber sector needs talented professionals — so why not stand as one of them?

 Live Chat
Live Chat